Unlock the Secret Code: Numbers to Letters
The art of cryptography has long fascinated humans, offering a unique blend of logic, mystery, and communication. At its core, cryptography transforms information into unreadable forms, only to be deciphered by those possessing the secret code. One of the simplest yet intriguing forms of this art involves the substitution of numbers for letters, creating a hidden language that can reveal profound messages or protect sensitive data. In this exploration, we delve into the world of number-letter cryptography, uncovering its principles, applications, and the rich history that has shaped this fascinating practice.
Cryptography is an ancient practice, with early civilizations using simple substitution ciphers to protect their messages. The evolution of cryptography is a testament to human ingenuity, as each breakthrough in code-breaking techniques has led to more sophisticated methods of encryption and decryption.
The Basics of Number-Letter Substitution

At its essence, number-letter substitution cryptography is a straightforward concept. Each letter of the alphabet is assigned a corresponding number, creating a unique numerical representation of words and phrases. This substitution can be done in a variety of ways, each with its own complexity and level of security.
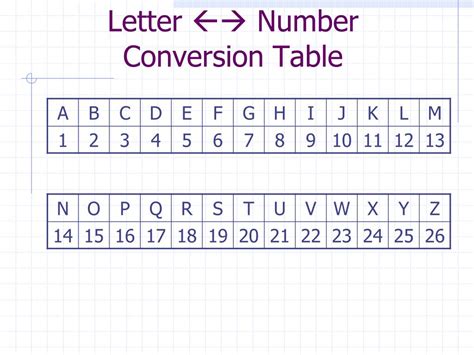
The most basic approach is to assign numbers sequentially, starting with ‘A’ as 1 and proceeding through the alphabet. For instance, ‘B’ would be 2, ‘C’ would be 3, and so on. While this method is simple to implement, it also makes the code easier to break, as patterns become apparent with longer messages.
More secure variations involve random assignments, where the numbers are not in sequential order. For example, ‘A’ could be 7, ‘B’ could be 25, and ‘C’ might be 13. This randomization adds a layer of complexity, making it harder for unauthorized individuals to decipher the message without the key.
Historical Applications
The use of number-letter substitution has a rich historical context, with notable applications spanning from ancient civilizations to modern times. One of the earliest known examples is the Caesar cipher, used by Julius Caesar himself to communicate with his generals. In this cipher, each letter is replaced by one that is three places down the alphabet. So, ‘A’ becomes ’D’, ‘B’ becomes ‘E’, and so forth.
During the Renaissance, the famous Italian mathematician and cryptographer, Leon Battista Alberti, developed a polyalphabetic cipher known as the Alberti cipher. This cipher used a complex system of disks, each with a different alphabet arrangement, to create a multi-layered encryption method that was ahead of its time.
In more recent history, number-letter substitution found use during World War II with the German Enigma machine. While the Enigma used a complex system of rotors and plugboards, the principle remained the same: substituting letters for numbers to create an encrypted message.
Modern Applications and Security Considerations
While the methods of number-letter substitution might seem simplistic in the digital age, they still hold relevance in certain contexts. For example, in the realm of physical security, a simple number-letter substitution can be used to create passcodes for locks or safe combinations. In these instances, the security lies not only in the substitution itself but also in the physical protection of the key.
However, in the digital world, where data can be easily intercepted and transmitted, number-letter substitution cryptography has limited use. Modern encryption methods, such as public-key cryptography, offer far more robust security measures. These methods use complex mathematical algorithms to encrypt data, making them far more secure than simple number-letter substitution.
Deciphering Techniques
Breaking a number-letter substitution cipher requires a combination of logical reasoning, pattern recognition, and, in some cases, sheer luck. For simpler ciphers, frequency analysis—the study of how often certain letters appear in a given language—can be a powerful tool. By analyzing the frequency of numbers in a cipher, one can make educated guesses about which number represents which letter.
More complex ciphers, especially those with random assignments, require a brute-force approach. This involves trying every possible combination of letters until the original message is revealed. However, this method can be time-consuming and is less practical for longer messages.
Practical Tips for Creating Secure Number-Letter Ciphers

For those interested in creating their own number-letter substitution ciphers, there are a few tips to keep in mind to enhance security:
- Use a random number generator to assign numbers to letters, ensuring a more unpredictable code.
- Consider creating a key that is separate from the message, adding an extra layer of security.
- Mix up the order of numbers and letters to create a more complex cipher.
- Avoid using common words or phrases, as these can be easily guessed.
Conclusion
Number-letter substitution cryptography, while seemingly basic, offers a fascinating glimpse into the world of code-making and breaking. Its historical significance, from ancient civilizations to wartime applications, highlights its enduring appeal and the constant evolution of human communication.
While number-letter substitution might not be the most secure form of cryptography in today’s digital world, its principles continue to underpin more complex encryption methods. As we continue to develop ever more sophisticated methods of protecting our data, the art of cryptography, with its blend of mathematics, logic, and creativity, remains an intriguing field of study.
How does number-letter substitution cryptography differ from other forms of encryption?
+Number-letter substitution cryptography is a simple form of encryption where each letter of the alphabet is replaced by a corresponding number. While it offers a basic level of security, more complex encryption methods, such as public-key cryptography, use mathematical algorithms to provide higher levels of protection.
What are some common challenges in deciphering number-letter substitution ciphers?
+Common challenges include the length of the message, as longer messages provide more data for analysis. Additionally, the complexity of the cipher, such as whether it uses random assignments or sequential numbers, can impact the difficulty of deciphering.
Can number-letter substitution cryptography be used in modern digital security?
+While number-letter substitution has historical significance and can still be useful in certain physical security contexts, it is not recommended for modern digital security due to its limited complexity and ease of deciphering.
What are some tips for creating a more secure number-letter substitution cipher?
+To enhance security, consider using a random number generator for assignments, creating a separate key, mixing up the order of numbers and letters, and avoiding common words or phrases.


