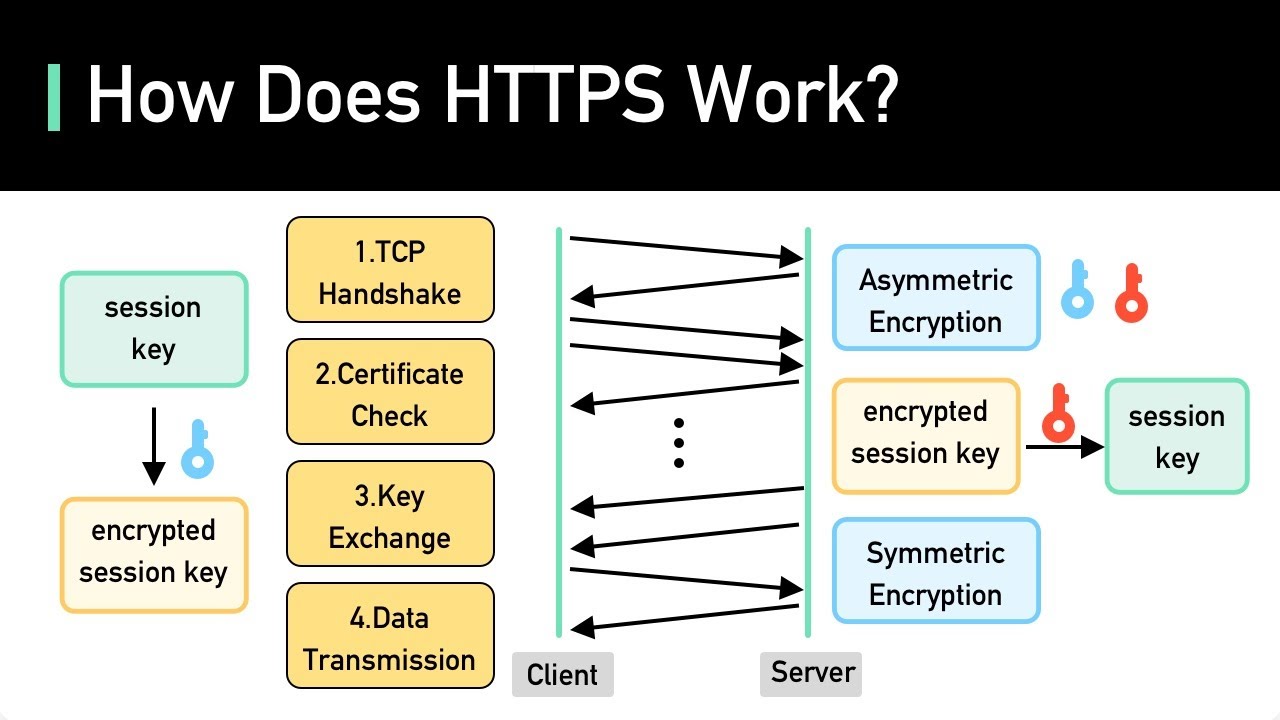
4 Key Steps for TLS Connection

The Transport Layer Security (TLS) protocol is a critical component of secure communication over the internet, ensuring data privacy and integrity during transmission. Understanding the steps involved in establishing a TLS connection is essential for maintaining a secure digital environment. In this article, we will delve into the intricacies of the TLS handshake process, exploring its four key steps and their significance in establishing a secure and reliable connection.
The TLS Handshake: A Secure Dance

The TLS handshake is a sophisticated process that allows two entities, typically a client (such as a web browser) and a server (a web server), to agree upon a set of cryptographic parameters and establish a secure connection. This handshake is a delicate dance of messages exchanged between the client and server, each step building upon the previous one to create a secure environment for data transmission.
Step 1: Client Hello

The TLS handshake begins with the client initiating the process by sending a Client Hello message to the server. This message serves as an introduction, providing essential information about the client’s capabilities and preferences. The Client Hello includes the following critical details:
- TLS Version: The client indicates the highest TLS version it supports, ensuring compatibility with the server.
- Cipher Suites: A list of encryption algorithms and key exchange methods supported by the client. This allows the server to choose an appropriate suite for secure communication.
- Random Data: A unique, random value generated by the client, used to create session-specific keys.
- Session ID: If the client has previously connected to the server, it may include a session ID to resume an existing session, speeding up the handshake process.
- Extensions: Additional information about the client’s capabilities, such as support for certificate compression or server name indication (SNI), which allows multiple hostnames to be served by a single IP address.
Example: Client Hello in Action
Let’s consider a scenario where a user, Alice, is attempting to access a secure website. Her web browser sends a Client Hello message to the website’s server, including the following details:
| TLS Version | TLS 1.3 |
|---|---|
| Cipher Suites | TLS_AES_256_GCM_SHA384, TLS_CHACHA20_POLY1305_SHA256 |
| Random Data | A 32-byte random value generated by Alice’s browser |
| Session ID | If Alice has visited the site before, a unique session ID is included. |
| Extensions | Server Name Indication (SNI) to indicate the desired hostname. |
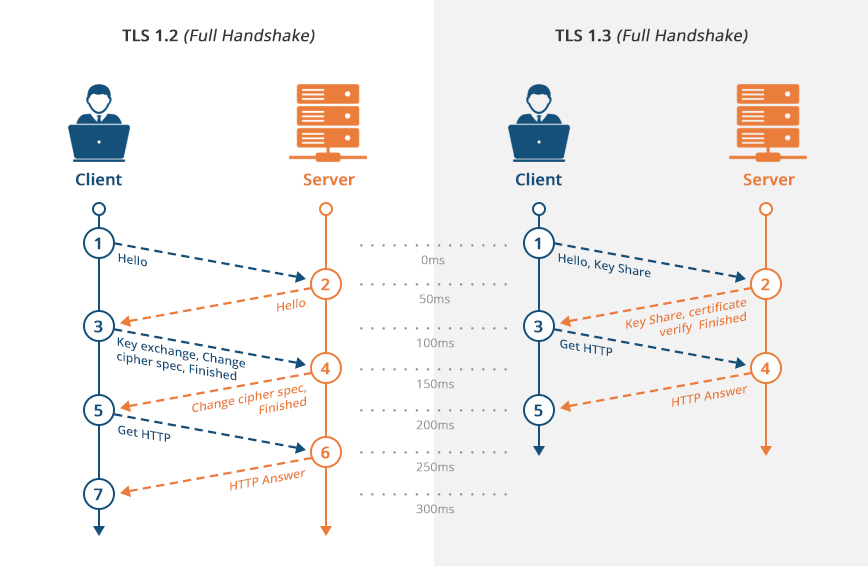
Step 2: Server Hello
Upon receiving the Client Hello, the server responds with its own Server Hello message. This message is a crucial part of the handshake, as it confirms the server’s agreement with the client’s proposed parameters and provides additional information necessary for establishing the secure connection.
The Server Hello includes the following key elements:
- TLS Version: The server acknowledges the TLS version it will use, based on the client's preference.
- Cipher Suite: The server selects a cipher suite from the list provided by the client, choosing the most secure and compatible option.
- Random Data: Similar to the client, the server generates a unique, random value to contribute to the creation of session-specific keys.
- Session ID: If the server accepts a resumed session, it echoes the session ID provided by the client. Otherwise, it generates a new one.
- Server Certificate: The server sends its X.509 digital certificate, which contains its public key and is signed by a trusted Certificate Authority (CA). This certificate allows the client to verify the server's identity.
Understanding the Server Certificate
The server certificate plays a vital role in the TLS handshake. It contains the server's public key, which is used to encrypt data sent from the client. Additionally, the certificate includes information about the server, such as its domain name and the CA that signed it. The client uses this information to validate the server's identity and ensure it is communicating with the intended entity.
Example: Server Hello Response
Continuing our scenario, the website’s server responds to Alice’s Client Hello with the following Server Hello message:
| TLS Version | TLS 1.3 |
|---|---|
| Cipher Suite | TLS_AES_256_GCM_SHA384 |
| Random Data | A 32-byte random value generated by the server |
| Session ID | If the server accepts a resumed session, it echoes Alice’s session ID. Otherwise, it generates a new one. |
| Server Certificate | An X.509 certificate containing the server’s public key and signed by a trusted CA. |
Step 3: Certificate Verification and Key Exchange
After receiving the Server Hello, the client verifies the server’s certificate to ensure it is authentic and belongs to the expected domain. This process involves several steps:
- Certificate Chain Validation: The client checks the certificate’s digital signature to verify its authenticity. It also examines the certificate’s chain of trust, ensuring that each certificate in the chain is signed by a trusted CA.
- Domain Name Validation: The client compares the Common Name (CN) field in the certificate with the domain name it is attempting to access. If there is a mismatch, the client may reject the connection as a potential man-in-the-middle attack.
- Revocation Checking: The client may check the certificate’s revocation status using mechanisms such as Online Certificate Status Protocol (OCSP) or Certificate Revocation Lists (CRLs). This step ensures that the certificate has not been revoked by the issuing CA.
Once the server's certificate is verified, the client and server engage in a Key Exchange protocol to securely negotiate a shared secret key. This key will be used to encrypt and decrypt data during the secure communication session.
Common Key Exchange Protocols
Several key exchange protocols are commonly used in TLS connections, each with its own strengths and weaknesses. Some popular options include:
- Diffie-Hellman (DH): Allows two parties to establish a shared secret key over an insecure channel. DH is often used in combination with other protocols to enhance security.
- Elliptic Curve Diffie-Hellman (ECDH): A variant of DH that uses elliptic curve cryptography, providing increased security with shorter key lengths.
- RSA Key Exchange: Utilizes the RSA public-key cryptosystem to exchange keys. RSA is widely used but may be less efficient than other protocols for large key sizes.
- Ephemeral Diffie-Hellman (DHE): A temporary, ephemeral version of DH, providing forward secrecy, where compromising past session keys does not compromise future sessions.
Example: Certificate Verification and Key Exchange
In our scenario, Alice’s browser verifies the server’s certificate by checking its digital signature, ensuring it is signed by a trusted CA. It also confirms that the certificate’s CN field matches the domain name she is trying to access. Once the certificate is verified, Alice’s browser and the server negotiate a shared secret key using the ECDH protocol, ensuring a secure and private connection.
Step 4: Change Cipher Spec and Finished Messages
With the shared secret key established, the client and server are ready to transition to the secure communication phase. This transition is initiated by the Change Cipher Spec message, sent by both the client and server, indicating their readiness to start encrypting data using the agreed-upon cipher suite and keys.
After sending the Change Cipher Spec message, the client and server exchange Finished messages. These messages confirm that the handshake process is complete and that both parties are ready to proceed with secure communication.
Example: Change Cipher Spec and Finished Messages
Alice’s browser and the server send Change Cipher Spec messages simultaneously, indicating their readiness to start encrypting data. Once these messages are exchanged, they follow up with Finished messages, confirming the successful completion of the TLS handshake.
Establishing a Secure Connection: Final Thoughts
The TLS handshake is a complex yet elegant process, ensuring the establishment of a secure and reliable connection between clients and servers. By understanding the four key steps outlined in this article, we gain insight into the critical role that TLS plays in securing our digital communications.
As we navigate the digital landscape, the importance of TLS cannot be overstated. From protecting sensitive data to maintaining the integrity of our online interactions, TLS provides a robust foundation for secure communication. By adhering to best practices and staying informed about emerging threats and advancements in TLS technology, we can continue to enhance the security and privacy of our online experiences.
What is the purpose of the TLS handshake process?
+The TLS handshake process establishes a secure and encrypted connection between a client and a server. It allows them to agree upon a set of cryptographic parameters, ensuring that data transmitted between them remains private and intact.
Why is it important to verify the server’s certificate during the TLS handshake?
+Certificate verification is crucial to ensure that the client is communicating with the intended server and not an imposter. It helps prevent man-in-the-middle attacks and ensures the integrity of the connection.
Can the TLS handshake process be optimized for better performance?
+Yes, various techniques can be employed to optimize the TLS handshake, such as using session resumption, enabling TLS false start, or utilizing techniques like TLS 1.3’s 0-RTT (zero round-trip time) to reduce the number of round trips required during the handshake.



