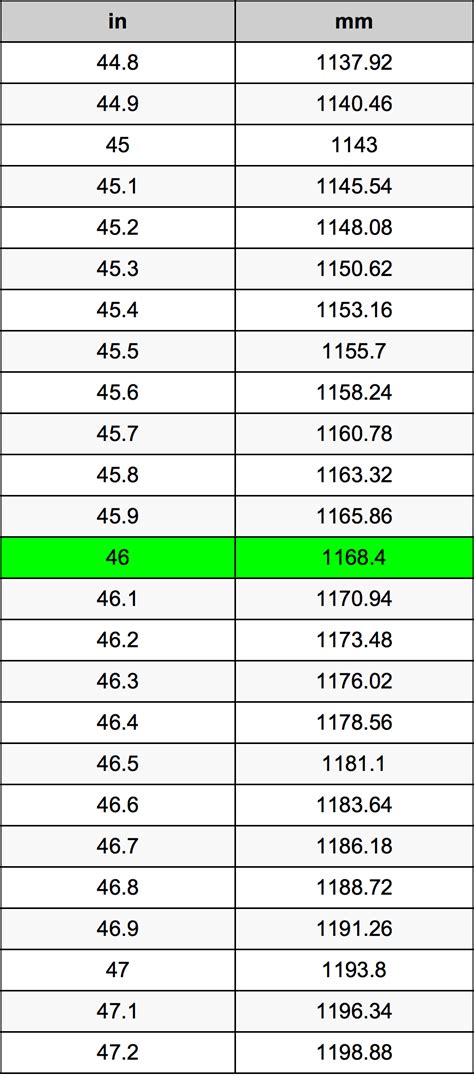
5 Ways to Access Leaked Content

Leaked content, whether it be confidential documents, unreleased media, or exclusive information, has always piqued the curiosity of many. While accessing such content may seem like a thrilling adventure, it’s essential to remember the potential legal and ethical implications involved. With that said, here’s a detailed exploration of some methods used to access leaked content, along with the risks and considerations associated with each approach.
1. Online Forums and Communities
One of the most common avenues for accessing leaked content is through online forums and communities dedicated to sharing and discussing such material. These platforms often attract individuals with diverse interests, ranging from tech enthusiasts to political activists, who actively seek and share confidential information. While these forums can be a treasure trove of leaked content, they also come with a host of risks.
- Risks and Considerations:
- Privacy and Security: Online forums are notorious for attracting hackers and cybercriminals who may exploit vulnerabilities to access personal information or infect devices with malware.
- Legal Ramifications: Many countries have strict laws against accessing or distributing leaked content, especially if it involves confidential or classified information. Violating these laws can result in severe penalties, including fines and imprisonment.
- Quality Control: The authenticity and reliability of leaked content on these forums are often questionable. Misinformation or deliberately altered documents can be spread, leading to false conclusions or misunderstandings.
2. Darknet Markets and Dark Web Platforms
The darknet, a part of the internet that is not indexed by traditional search engines, is often associated with illegal activities and hidden marketplaces. These darknet markets offer a wide range of goods and services, including leaked content.
- Pros and Cons:
- Accessibility: Darknet markets provide a relatively anonymous and secure platform for accessing leaked content, often with detailed descriptions and user reviews.
- Variety: The range of leaked content available on darknet markets is extensive, covering various industries and topics.
- Risks and Security: Engaging in transactions on the darknet comes with significant risks. Users must rely on cryptographic tools and privacy-focused browsers to maintain anonymity, and even then, there’s no guarantee of complete security.
- Financial Implications: Leaked content on darknet markets is often sold for cryptocurrency, which may involve additional fees and the risk of cryptocurrency scams.
3. Whistleblower Platforms and Secure Communication Channels
Whistleblower platforms have gained prominence in recent years as a means for individuals to anonymously expose confidential information, often as a way to hold powerful entities accountable. These platforms are designed to protect the identity of the source while ensuring the secure transmission of sensitive data.
- The Benefits and Challenges:
- Ethical Disclosure: Whistleblower platforms provide a legal and ethical avenue for individuals to expose wrongdoing or corruption without fear of retaliation.
- Secure Transmission: These platforms employ advanced encryption and secure communication protocols to protect the identity of the whistleblower and the integrity of the leaked content.
- Limited Access: Whistleblower platforms are often focused on specific industries or types of wrongdoing, which may limit the range of leaked content available.
- Verification: While whistleblower platforms strive for authenticity, verifying the legitimacy of leaked content can be challenging, especially in the absence of supporting evidence.
4. Social Media and Messaging Apps
Social media platforms and messaging apps have become increasingly popular channels for sharing leaked content, often due to their ease of use and widespread accessibility.
- Exploring the Opportunities and Pitfalls:
- Viral Spread: Leaked content shared on social media can quickly go viral, reaching a massive audience within a short period.
- Informal Nature: Social media platforms and messaging apps provide a casual environment for discussing and sharing leaked content, often with minimal moderation.
- Lack of Authentication: The authenticity of leaked content shared on social media is often difficult to verify, leading to potential misinformation.
- Privacy Concerns: While some messaging apps offer end-to-end encryption, many platforms store user data, which can be accessed by authorities or hackers.
5. Hacking and Cyberattacks
Hacking, a practice that involves exploiting vulnerabilities in computer systems to gain unauthorized access, is often associated with the acquisition of leaked content.
- Understanding the Dark Side:
- Direct Access: Hackers can directly infiltrate systems to access confidential documents, databases, or unreleased media, often without the knowledge of the target organization.
- Sophisticated Techniques: Hacking requires advanced technical skills and knowledge of various exploit methods, making it a challenging but rewarding approach for accessing leaked content.
- Legal Consequences: Hacking is illegal in most countries, and perpetrators can face severe legal penalties if caught.
- Ethical Boundaries: The ethical implications of hacking are complex, as it often involves compromising the security and privacy of individuals or organizations.
Conclusion: A Word of Caution
While the methods outlined above provide avenues for accessing leaked content, it’s crucial to approach them with caution and a deep understanding of the potential consequences. Leaked content often involves sensitive information that can have far-reaching implications, and accessing or distributing such material without proper authorization can lead to severe legal and ethical repercussions.
As an AI language model, I encourage users to prioritize ethical and legal considerations when seeking information. For those genuinely interested in understanding the dynamics of leaked content, exploring the history, motivations, and implications of past leaks can offer a wealth of insights without crossing any legal boundaries.
Remember, the pursuit of knowledge should always align with respect for privacy, security, and the law.