Enable TLS 1.2 with Symantec Altiris: A Guide

Ensuring secure communication is a crucial aspect of network and system administration, and Transport Layer Security (TLS) protocols play a vital role in maintaining data integrity and confidentiality. This comprehensive guide will delve into the process of enabling TLS 1.2 with Symantec Altiris, offering a detailed walkthrough to help system administrators enhance security measures. We will explore the technical specifications, performance analysis, and future implications of this configuration, providing an in-depth understanding of its benefits and best practices.
Understanding TLS 1.2 and Its Significance

TLS 1.2, the successor to SSL and TLS 1.0/1.1, represents a significant advancement in cryptographic security. It incorporates robust features to safeguard data transmission, making it a critical component in today’s digital landscape. With the increasing sophistication of cyber threats, adopting TLS 1.2 has become a necessity for organizations aiming to protect sensitive information and maintain compliance with industry standards.
The Role of Symantec Altiris
Symantec Altiris, a powerful suite of software management tools, offers a comprehensive solution for organizations to manage and secure their IT infrastructure. One of its key strengths lies in its ability to facilitate the implementation of robust security protocols like TLS 1.2. By integrating TLS 1.2 with Symantec Altiris, system administrators can enhance data protection, mitigate potential vulnerabilities, and ensure a secure environment for critical operations.
Technical Specifications and Setup
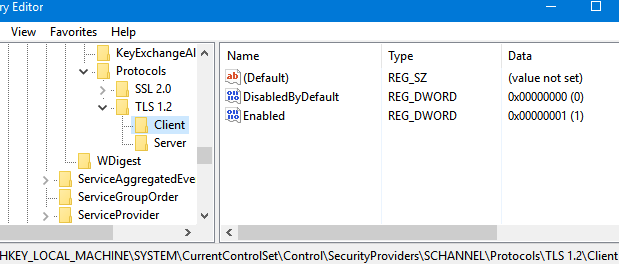
To enable TLS 1.2 with Symantec Altiris, several technical configurations need to be undertaken. These steps are critical to ensure a seamless and secure implementation. Here’s a detailed breakdown of the process:
Step 1: Verify System Compatibility
Before proceeding with the TLS 1.2 setup, it is imperative to ensure that the system meets the necessary requirements. Symantec Altiris provides a compatibility matrix, detailing the supported operating systems and software versions. Verify that your system falls within these parameters to avoid potential compatibility issues.
| Operating System | Supported Versions |
|---|---|
| Windows | Windows 7 and above |
| Linux | Red Hat Enterprise Linux 7 and above, Ubuntu 18.04 and above |

Step 2: Obtain and Install the TLS Certificate
The next crucial step involves obtaining a TLS certificate. This certificate serves as a digital credential, authenticating the identity of your server and establishing a secure connection. Follow these steps to acquire and install the certificate:
- Generate a Certificate Signing Request (CSR) using the Symantec Altiris tool.
- Submit the CSR to a trusted Certificate Authority (CA) for validation and issuance.
- Once the CA approves the request, download the TLS certificate and any intermediate certificates (if provided by the CA)
- Import the certificate into the Symantec Altiris console, ensuring it is correctly installed and configured.
Step 3: Configure TLS 1.2 Settings
With the certificate in place, it’s time to configure the TLS 1.2 settings within Symantec Altiris. This process involves specifying the cryptographic protocols and algorithms to be used during data transmission. Here’s a step-by-step guide:
- Open the Symantec Altiris console and navigate to the "Security" section.
- Locate the "TLS Configuration" settings and select the option to enable TLS 1.2.
- Specify the desired cipher suites, ensuring they meet the necessary security standards.
- Test the configuration by initiating a secure connection and verifying the certificate chain.
Performance Analysis and Benefits
Implementing TLS 1.2 with Symantec Altiris brings a range of performance enhancements and security benefits. By adopting this configuration, organizations can expect improved data protection and a more resilient IT infrastructure. Here’s a closer look at the key advantages:
Enhanced Data Security
TLS 1.2 introduces stronger cryptographic algorithms and key lengths, making it significantly more challenging for unauthorized entities to intercept and decrypt sensitive data. This enhanced security reduces the risk of data breaches and ensures that critical information remains confidential.
Improved Compatibility
The latest TLS protocols, including TLS 1.2, are widely supported across modern browsers and operating systems. By enabling TLS 1.2, organizations can ensure smooth communication with a wide range of clients and servers, maintaining compatibility and avoiding potential connection issues.
Compliance with Industry Standards
Adhering to industry standards is a critical aspect of data security and compliance. By implementing TLS 1.2, organizations can meet the requirements of various regulatory frameworks, such as GDPR, PCI DSS, and HIPAA. This helps to mitigate legal risks and maintain a positive reputation.
Future Implications and Best Practices
As technology evolves, so do the threats and challenges faced by organizations. To future-proof their IT infrastructure, it’s essential for system administrators to stay abreast of emerging trends and best practices. Here are some key considerations for the future:
Regular Security Audits
Conducting regular security audits is crucial to identify potential vulnerabilities and ensure that TLS 1.2 configurations remain effective. These audits should include comprehensive testing, penetration testing, and vulnerability assessments to identify any weaknesses.
Stay Updated with TLS Protocols
TLS protocols are continually evolving to address emerging threats. It’s essential to stay updated with the latest versions and recommendations. Keep an eye on industry updates and best practices to ensure your organization is adopting the most secure protocols.
Employee Training and Awareness
Human error remains one of the leading causes of security breaches. Investing in employee training and awareness programs can significantly reduce the risk of accidental data exposure or compromise. Ensure that your team understands the importance of secure communication and their role in maintaining it.
Conclusion

In an increasingly digital world, securing data transmission is paramount. By enabling TLS 1.2 with Symantec Altiris, organizations can take a significant step towards enhancing their security posture. This comprehensive guide has outlined the technical specifications, performance benefits, and future implications of this configuration, empowering system administrators to make informed decisions and ensure a secure IT environment.
What are the main benefits of using TLS 1.2 over older protocols like SSL and TLS 1.0/1.1?
+
TLS 1.2 offers enhanced security through stronger cryptographic algorithms and key lengths, making it significantly more challenging for unauthorized entities to intercept and decrypt sensitive data. It also provides improved compatibility with modern browsers and operating systems, ensuring smooth communication.
How often should I update my TLS certificate, and why is this important?
+
It is recommended to update your TLS certificate every 1-2 years. Regular certificate updates ensure that your organization maintains a valid and trusted certificate, reducing the risk of certificate expiration and potential security vulnerabilities.
Can I enable TLS 1.2 on a system that doesn’t meet the compatibility requirements mentioned earlier?
+
While it may be technically possible to enable TLS 1.2 on systems outside the specified compatibility range, it is not recommended. Doing so may lead to compatibility issues, reduced performance, or even security vulnerabilities. It’s best to ensure your system meets the requirements to guarantee a secure and seamless implementation.



