Solve Connectivity Issues: Firewall Debugging 101
Welcome to the world of network troubleshooting, where understanding and resolving connectivity issues is a crucial skill for any IT professional. In this comprehensive guide, we'll delve into the art of firewall debugging, exploring the common problems that disrupt network connectivity and providing expert strategies to solve them efficiently. Whether you're a seasoned network administrator or a curious IT enthusiast, this article will equip you with the knowledge and tools to tackle firewall-related challenges head-on.
Demystifying Firewall Debugging: A Necessary Skill

Firewalls, the guardians of network security, play a vital role in safeguarding our digital realms. However, when they misbehave, they can cause headaches and disrupt the smooth flow of data. Firewall debugging is an essential skill that empowers IT professionals to identify and rectify connectivity problems, ensuring seamless communication between devices and networks.
Understanding Common Firewall Issues

Before we dive into the debugging process, let’s familiarize ourselves with the most prevalent firewall issues that often lead to connectivity woes.
Misconfigured Rules
Firewall rules are the backbone of network security, dictating which traffic is allowed and which is blocked. Misconfigured rules can inadvertently block legitimate traffic, causing connectivity issues. Common mistakes include overly restrictive rules, missing rules, or conflicting configurations.
Port Blockages
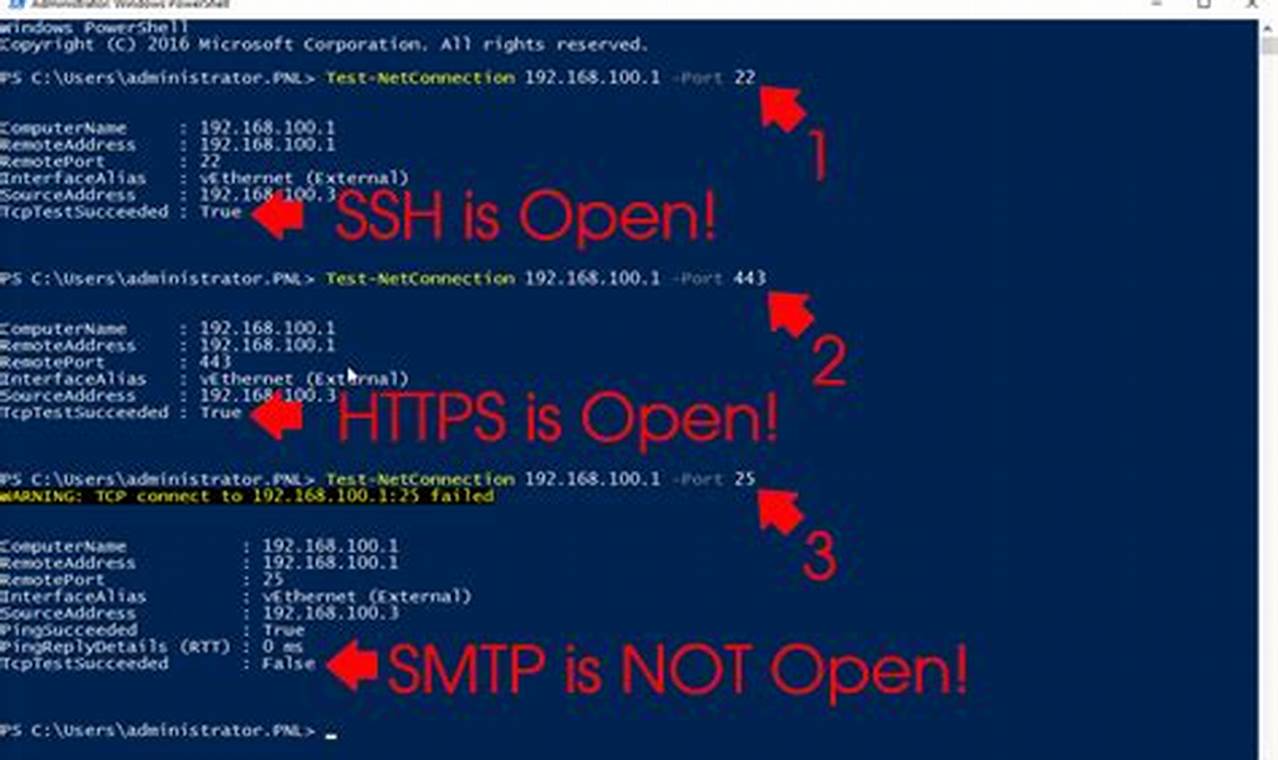
Certain applications and services rely on specific ports to function correctly. When these ports are blocked by the firewall, it can lead to connection failures. Common culprits include accidental blocking of standard ports like 80 (HTTP) or 443 (HTTPS) during rule configuration.
IP Address Restrictions
Firewalls often employ IP address-based access control, allowing or denying access based on the IP address of the requesting device. Misconfigurations here can result in authorized users being blocked or unauthorized users gaining access.
Outdated Firewall Software
Like any software, firewalls require regular updates to address security vulnerabilities and improve performance. Outdated firewall software can introduce bugs, compatibility issues, and security loopholes, leading to connectivity problems.
The Firewall Debugging Process: A Step-by-Step Guide
Now that we’ve identified the common culprits, let’s embark on a systematic journey to debug and resolve firewall-related connectivity issues.
Step 1: Identify the Problem
The first step in any debugging process is to clearly define the problem. Gather information from affected users, log files, and network monitoring tools to understand the nature and scope of the connectivity issue. Is it affecting a specific application, a particular user, or the entire network? Identifying the problem accurately is crucial for devising an effective solution.
Step 2: Check Firewall Rules
Examine the firewall rules to ensure they align with the intended network policies. Look for rules that may have been accidentally added, removed, or modified, leading to the current connectivity problem. Compare the rules with the desired configuration to identify any discrepancies.
Step 3: Verify Port Configurations
Ensure that the necessary ports are open and accessible for the affected applications or services. Check the firewall rules, and if needed, adjust the port configurations to allow the required traffic. Remember to strike a balance between security and functionality, opening only the necessary ports.
Step 4: Audit IP Address Access Controls
Review the IP address-based access controls to ensure they are correctly configured. Verify that authorized IP addresses have access and that unauthorized IP addresses are appropriately restricted. This step is crucial to maintaining network security while allowing legitimate users access.
Step 5: Update Firewall Software
Keep your firewall software up-to-date to benefit from the latest security patches and performance improvements. Regular updates help prevent compatibility issues and reduce the risk of connectivity problems caused by outdated software.
Step 6: Test and Monitor
After implementing the necessary changes, test the network connectivity to ensure the issue is resolved. Use network monitoring tools to observe the traffic flow and verify that the desired applications and services are functioning as expected. Regular monitoring helps detect any potential issues early on.
Advanced Firewall Debugging Techniques
While the above steps cover the fundamentals of firewall debugging, sometimes more complex issues require advanced techniques. Here are some expert strategies to tackle stubborn connectivity problems.
Packet Capturing and Analysis
Utilize packet capturing tools to capture and analyze network traffic. This technique helps identify anomalies, such as dropped packets or unexpected routing, that may be causing connectivity issues. Analyzing the captured packets can provide valuable insights into the root cause of the problem.
Firewall Logging and Troubleshooting
Enable detailed logging on your firewall to capture valuable information about network traffic and events. Reviewing the logs can reveal patterns, errors, or security breaches that may be impacting connectivity. Troubleshooting based on log analysis is an effective way to pinpoint and resolve complex issues.
Network Segmentation and Testing
Divide your network into segments and test each segment’s connectivity independently. This technique helps isolate the problem to a specific segment, making it easier to identify and resolve issues. Network segmentation also enhances security by containing potential threats within isolated segments.
Collaboration and Knowledge Sharing
Networking with fellow IT professionals and participating in online communities can provide valuable insights and solutions to complex firewall debugging challenges. Sharing knowledge and experiences can lead to innovative solutions and a deeper understanding of firewall behavior.
Best Practices for Effective Firewall Debugging

To excel in firewall debugging, adopting best practices is essential. Here are some expert recommendations to enhance your troubleshooting skills.
Document and Version Control
Maintain a comprehensive documentation of your firewall configurations, including rules, port mappings, and access controls. Use version control systems to track changes, making it easier to revert to previous configurations if needed. Documentation ensures consistency and facilitates knowledge sharing within your team.
Regular Firewall Audits
Conduct regular audits of your firewall configurations to identify potential issues and ensure compliance with security policies. Audits help catch misconfigurations early and prevent connectivity problems before they impact users.
Keep an Eye on Emerging Threats
Stay informed about emerging security threats and vulnerabilities that may impact your network. Subscribe to security newsletters, follow reputable security blogs, and attend industry conferences to stay ahead of the curve. Being proactive about security threats helps you anticipate and mitigate potential issues before they cause connectivity disruptions.
Continuous Learning and Skill Development
Firewall technology is constantly evolving, and staying up-to-date with the latest advancements is crucial. Invest time in continuous learning, attending training programs, and earning certifications to enhance your firewall debugging skills. Staying current ensures you can tackle new challenges and adapt to changing network landscapes.
Future Trends in Firewall Technology
As technology advances, firewall solutions are evolving to meet the growing demands of modern networks. Here’s a glimpse into the future of firewall technology.
Artificial Intelligence and Machine Learning
AI and machine learning are revolutionizing network security, enabling firewalls to learn and adapt to emerging threats. These technologies can analyze network behavior, identify anomalies, and make real-time decisions to enhance security and optimize network performance.
Cloud-Based Firewalls
The rise of cloud computing has led to the development of cloud-based firewalls, offering scalability, flexibility, and centralized management. Cloud-based firewalls provide robust security for cloud-hosted applications and services, ensuring seamless connectivity and protection.
Zero-Trust Security Models
The traditional perimeter-based security model is being challenged by the zero-trust approach, which assumes that no user or device should be trusted by default. Zero-trust firewalls implement strict access controls and continuous verification, ensuring that only authorized users and devices can access network resources.
Conclusion: Empowering Network Administrators
Firewall debugging is an essential skill for network administrators, empowering them to resolve connectivity issues efficiently and ensure a seamless user experience. By understanding the common firewall issues and adopting a systematic debugging process, IT professionals can troubleshoot and resolve problems effectively. Embracing advanced techniques, best practices, and future trends in firewall technology further enhances their ability to safeguard and optimize network connectivity.
As we navigate the ever-evolving landscape of network security, the expertise gained through firewall debugging becomes a valuable asset. With the knowledge and tools presented in this guide, you are well-equipped to tackle connectivity challenges and contribute to a secure and efficient digital world.
How often should I update my firewall software?
+It is recommended to update your firewall software regularly, typically every 3-6 months or whenever new security patches and updates are released. Regular updates help maintain optimal performance and address potential vulnerabilities.
What are some common signs of a firewall-related connectivity issue?
+Signs of a firewall-related connectivity issue may include slow network speeds, dropped connections, specific applications not functioning correctly, or errors indicating network access denied. Monitoring these symptoms can help identify potential firewall issues.
How can I optimize my firewall rules for better performance?
+Optimizing firewall rules involves striking a balance between security and performance. Avoid overly restrictive rules that may inadvertently block legitimate traffic. Regularly review and audit your rules to ensure they align with your network’s needs and security policies.
What is the role of AI in firewall technology?
+AI plays a crucial role in firewall technology by enabling advanced threat detection and response. AI-powered firewalls can analyze network behavior, identify anomalies, and make real-time decisions to enhance security and optimize network performance. This technology is revolutionizing network security.